
The public sector has become a favored target for cybercriminals globally. Not only for their valuable data but because their legacy security is being outpaced by the technological evolution.
Difenda understands that public sector organizations face unique challenges when it comes to cybersecurity. A lack of skilled personnel and staffing shortages can cause difficulties when creating an effective security program. But strict compliance mandates and budgetary uncertainties cause their own host of problems.
In a recent webinar, Megan Miller, and Jamie Hari, Difenda’s cybersecurity experts discussed innovative strategies for public sector organizations to protect their environment. This webinar covered building an integrated security approach, maximizing on your current security investments and our Microsoft-backed attack-driven approach to identify threat hunt criteria from IT to OT and beyond.
Here are some of the biggest takeaways from the event.
Top security challenges in the public sector
The public sector has experienced a series of pain points as a result of rapid changes to cybersecurity over the past two years. These include:
- New complex frameworks, regulations, and standards: Currently, overlapping and complex frameworks are causing administrative and financial challenges. Luckily, many agencies are looking to simplify these standards and make regulations easier to navigate in the near future.
- Operation efforts are increasing but resources are stagnant: With remote work expanding the threat surface and an increase in attack complexity, organizations need to be more efficient with their tooling. The public sector is constantly experiencing a shortage of resources, training issues and high turnover rates. It is time to consolidate services and do more with less.
- Increased threats around critical infrastructure and operational technology: Operational technology (OT) has now become the target of thousands of cyber-attacks. Threat actors are consistently leveraging OT environments as the point of entry or even as the end goal of attacks. The public sector needs to think about their organizations more wholistically and create strategies that marry incidence response, remediation and personnel for both IT and OT.
- Increased threats from organized crime and nation-state actors: New tools and technology are constantly developed by nation-state actors and are becoming available on the dark web. As seen by multiple attacks in the past few years, such as with Canada Revenue Agency, the public sector is not immune. Luckily, Microsoft is investing in tools and capabilities to address these issues, specifically in the public sector.

Why are public sector security programs failing?
The idea of an internal cybersecurity team was the goal two years ago. But, with remote working, the lack of cybersecurity professionals available, and of course reduced funding, that idea is now an impossibility. Leveraging shared models and cooperative services is the only way to keep up with demand today.
Over the past two years, integration has been key for cybersecurity and threat actors. Increased integration allows remote workers to do more and connect better with their teams. But it also allows attackers to navigate further into security networks. Unfortunately, integration capabilities have outpaced many internal security teams’ abilities to keep up. Moving forward, all cybersecurity programs need to refocus on leveraging external automation and orchestration capabilities to protect their highly integrated environments.
Additionally, security programs need to be organizational efforts encompassing all the people, processes, and technologies involved. One of the key reasons public sector security programs fail is a lack of organizational buy-in, especially from the senior level. For a successful program, there need to be comprehensive incidence response processes that include the marketing department, human resources, legal department and public relations, not just the IT staff.
The modern approach to managed security services
Often, in public sector organizations changes to security posture revolve around budget or a security event. The challenge is that those don’t often align with establishing a comprehensive framework. Creating a simple roadmap to a sustainable defense will accelerate modernization and hit targets all without blowing your budget.
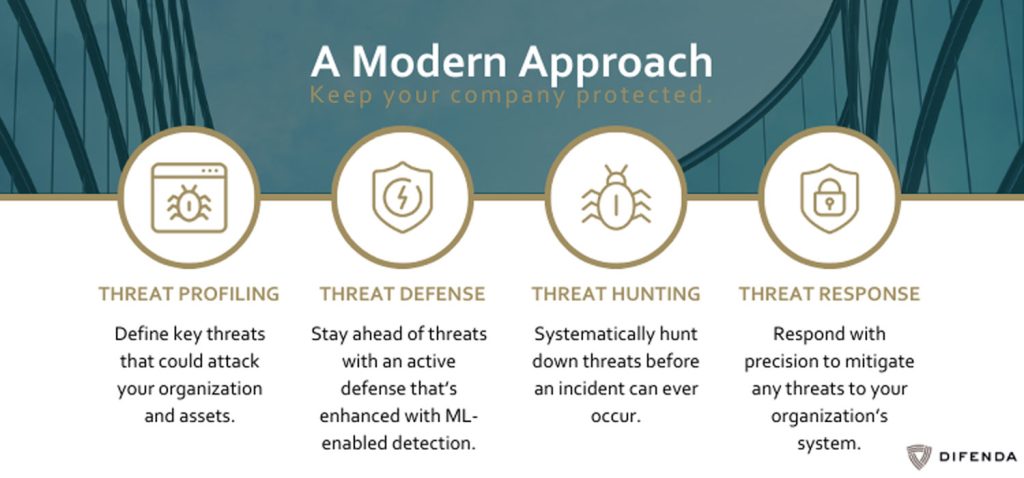
Hari outlined four key stages to an effective cybersecurity program in today’s public sector environment:
- Public sector organizations need to start by getting an understanding of their current assets. Not just listing physical locations of technology but, understanding where their sensitive data lives. By pre-classifying and maintaining good asset inventory hygiene, you set the foundation to make intelligent decisions about your security program.
- The next step is leveraging threat defenses that your business already has. Gaining visibility into your network and the ability to respond and block threats in real-time will be crucial to your threat defense. Attackers are leveraging the dark corners of your environment to maintain their hold on your network. Organizations need machine learning power such as advanced managed detection and response (MDR) capabilities to ensure attackers do not remain in their network undetected.
- Human-based intelligence is key to any great security program. Your personnel help protect your network in two main ways: proactive threat hunting and reactive patching in response to global activities. This is not an easy task, which is why many people outsource their advanced vulnerability management capabilities to external MSSP’s like Difenda.
- Your business’s threat response is the most important aspect of your security program. What are your organization’s capabilities when an attack occurs? Do you have an Incidence response plan? Who is involved? Regardless of what your plan looks like, it needs to include the entire organization and leverage all the tools you have at your disposal. Being prepared and having the ability to respond quickly is the best way to mitigate any threats to your network.
How can you maximize your Microsoft Security investment?
Many businesses are unaware of what Microsoft products and services exist, which ones they are already invested in and which can help reach their business goals. In order to maximize on your Microsoft Security program, you need to understand your current controls, where you have gaps and what tools your license provides. Difenda has created many helpful resources to assist in your Microsoft Security program’s success:
- Determine if you are missing out on valuable Microsoft tools and services included in your licensing with Difenda’s End-to-End Microsoft Security Roadmap.
- Discover how Difenda’s professional services can help design, implement, configure and maximize your Microsoft Security investment. Download our End-to-End Security Roadmap.
- Understand your options for Microsoft Funding & Incentives. Download our eBook!
Wrapping up
Miller and Hari offered a lot of valuable information during the webinar for organizations interested in maximizing their Microsoft Security investment. From integrating your IT and OT environments to the need for external support, they made it clear that as organizations need to be doing more with less; consolidation is the key to successful security programs in the public sector.


